Cyberwar is the name given to conflicts that take place in the digital sphere, where weapons and soldiers give way to malware and hackers. In such a scenario, attacks by a country – or organization – on the enemy’s main objective is to destabilize systems controlling infrastructure, networks, telecommunications, and even devices connected to the population, in efforts of varying levels of complexity and impact.
Unlike the isolated actions of hackers, attacks classified as cyber warfare operations aim to cause real damage from virtual attacks. Taking down the internal network of power plants to promote a blackout in the enemy country, compromising lines of communication to impair the circulation of information, interfering with air traffic monitoring and platforms that perform logistical control of the circulation of products and services are examples of tactics that can be orchestrated in virtual conflicts.
The discussion about the meaning and impacts of cyberwarfare has been on the rise due to the conflict between Russia and Ukraine. As tensions have intensified, it is believed that the war may go beyond the physical battlefields and into the virtual environment. Below, Techidence explains what cyberwarfare is and how it works, the most common types of attacks, and how citizens can protect themselves.
The Cyber War Between Russia and Ukraine
Until the publication of this article, the conflict in Eastern Europe has not produced, in the online environment, episodes of high gravity between the two countries. However, data from Check Point Research show that online attacks against Ukrainian military and government sectors increased by 196% in the first three days after the Russian invasion.
Experts interviewed by the British newspaper The Guardian ponder that, although the two countries have a great capacity to attack in this sphere, there is an element of deterrence that may be preventing actions of greater impact. Let us explain: to discourage attacks, a country positions itself as capable of causing severe damage to rivals. It is, therefore, a kind of “security”.
Thinking about the war in Ukraine, Russia may be reticent about unleashing actions with a great capacity to generate damage, for fear that a Ukrainian counterattack would happen in greater intensity and cause severe impact on Russian territory.
One factor that has attracted attention, but has yet to prove relevant, is the promise of the activist group Anonymous to concentrate efforts on attacks on Russian services, websites, and resources. The group has positioned itself as opposed to war and holds the Russian country responsible for the conflict.
In addition, an informal army of about 300,000 hackers has volunteered to support Ukraine in the cyberwar against Russia, British newspaper The Guardian reports. Recruited by the Ukrainian government, the so-called “IT army” meets in a Telegram Messenger group, where they orchestrate missions against Russian government websites and Russian media outlets that are partisan to Vladimir Putin.
Tension is old
Although the invasion of Ukrainian territory took place only in 2022, tensions between the two countries are not new and have been evolving over the past decade. In 2014, there was evidence of Russian hacker actions against the neighboring country since before the annexation of Crimea to Russia. One example was the attack directed at the Ukrainian electricity distribution infrastructure. The action caused blackouts and compromised the country’s reaction to the seizure of the peninsula.
In January of this year, prior to the military invasion, Russian hackers carried out a series of actions that took down public administration websites in the neighboring nation and also produced digital vandalism on web pages hosted in Ukraine.
What Cyberwar is and How It Works

In a cyberwar, one country may list strategic targets of an adversary nation and attack them. In general, the goal is to compromise the enemy’s operations by affecting the population’s standards of living – or the fighting ability of its armed forces – as a way to pressure the adversary into submission.
In this sense, a specialized force of hackers can attack the telecommunications infrastructure so that there is a disruption to the enemy country’s communication and information channels. Another possible scenario is the attack on power distribution and generation stations, intending to cause blackouts that could damage the day-to-day life of the population and the enemy military forces.
In addition to the aforementioned attacks, forces deployed in a cyber conflict can also exploit enemy secrets. If a hacker manages to break into rival forces’ systems, he may have access to strategic military data, and this can become a relevant factor in operations.
Several countries have intelligence organizations that are responsible for so-called counterintelligence – actions to prevent such attacks in case of conflict – as well as teams in charge of organizing and triggering actions to exploit gaps and vulnerabilities in a conflict.
Attack types
Cyberwar attacks offer the same variety as everyday hacker actions. At the simplest level, an attack might focus solely on denial of service (DDoS) actions, in which a group can mobilize a large number of machines to access a single web address, thereby overwhelming it.
If the scale of the attack is really large – something in the hundreds of thousands or millions of access attempts per second – the server hosting the resource may be unable to work and lead to a service outage. In a cyberwar, such an action could be organized to take government communication channels offline to misinform the population or compromise the public’s ability to access relevant data regarding conflict, evasion from threatened areas, etc.
The promotion of disinformation is also considered a form of attack. Fake news and rumors can cause confusion, increase the level of tension in the population, and disrupt efforts to evacuate areas under attack. In addition, fake news can also create a climate of distrust in the public towards the authorities, compromising internal support for a major land defense effort, for example.
Cyber forces can also focus on obtaining sensitive information from the adversary government. If successful, these actions can collect strategically relevant data to the aftermath of war, as well as better educate the country’s posture in terms of a peace agreement.
A more serious model of cyberattack – and one that is usually more associated with this type of operation – are offensive actions in which hackers end up directly compromising the organization of a country’s infrastructure. A group that has access to a country’s internal power grid, for example, can shut down the electricity supply, pressuring the population against the government and compromising the ability of adversary military forces.
In addition to attacks on the power grid, other public services can also become targets, such as the financial market, drinking water distribution services, telecommunications, and the security sector.
Examples of cyber-warfare
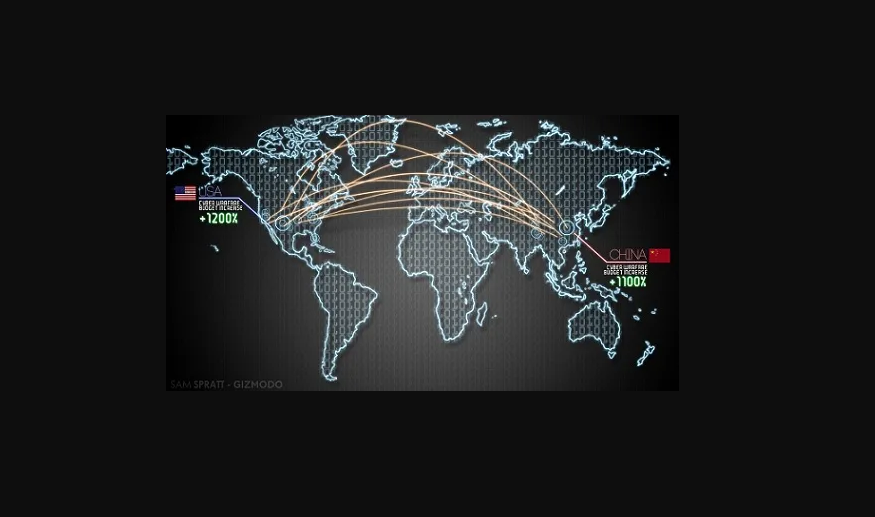
Google vs. China
In 2009, Google’s Chinese division was the target of an attack that violated the integrity of human rights activists living in the country. The intrusion was considered to be of high severity. In addition to users’ emails, there was access to the internal codes of the company’s services. Those responsible were never identified, but it is believed that Chinese security agents interested in documenting the movements of opponents of the regime were behind the attack.
First hybrid war and Russian-promoted attacks
In the year 2007, Estonia became the target of a concentrated denial of service action from a wide range of websites in the country. The action was in response to a decision by the administration of the country’s capital to remove a statue installed during the Soviet period when Estonia was part of the USSR. Experts also point to Russia’s actions in the war in Georgia in 2008, but, as the country had only 7% of the population connected at the time, the impact of the attacks ended up not being so decisive.
In both cases, there is no precise information regarding who was responsible. However, it is believed that the attacks originated from Russian-based organizations and received government support. While in the Estonian episode the reaction has to do with historical issues linked to Estonia’s independence from Russian rule, the second occurrence is more relevant: the use of hacker attacks in preparation for a traditional military mobilization is identified by many as the first hybrid war in history.
The malware that delayed a nuclear program
In 2010, security experts found Stuxnet: a malware that caused computers running antivirus to crash. Being extremely sophisticated, the virus had escaped the control of its creators and was spreading on specialized computers to control machines. After much analysis, it was discovered that Stuxnet had been carefully designed and developed to destroy the uranium enrichment centrifuges of the Iranian nuclear program. It is estimated that the virus destroyed over a thousand centrifuges between 2009 and 2010.
Iran has never taken a position on the episode, and neither have the two countries that are held responsible, the United States and Israel. Established in 2005, the partnership between the intelligence services of the two nations was named “Operation Olympic Games” and focused on the production of cyber weapons as a way to cause damage and hinder the progress of the Iranian nuclear program. This geopolitical issue is considered extremely sensitive to the interests of Israel, a historic ally of the United States.
Operations by the NSA, the US security agency, are also part of episodes that show the destructive power of cyber warfare. With the use of a series of sophisticated resources, the agency had a data collection network that allowed access to internal communications of leaders from countries around the world.
How to defend yourself in a cyberwar
From the national point of view, who determines the level of resistance of the country to cyber-attacks are the public administration and the defense forces. It is up to the population to have an interest in the subject and know how to pressure the responsible agents so that the country can offer good defense capability in case it becomes the target of some hostile country or organization.
But some measures can be taken by ordinary citizens in their daily lives to hinder the enemy’s actions. In a DDoS attack, for example, hackers need a network of infected machines to carry out their incursion. Therefore, if citizens are careful to keep the security of their devices up to date, the capacity for contamination decreases and the adversary’s room for maneuver becomes limited.
In addition, care when accessing the information on the Internet can be fundamental for a public servant not to open a malicious link and contaminate a network of state services. Good security practices applied at work can also be essential for the enemy to face greater difficulty when trying to destroy services and compromise the operation of companies, an action necessary to harm the economy.
This post may contain affiliate links, which means that I may receive a commission if you make a purchase using these links. As an Amazon Associate, I earn from qualifying purchases.

